Purple Teams through VECTR™ generates success defense metrics and helps align Red and Blue Teams towards the same mission: protecting the organization by discovering and plugging detection gaps.
Installing Vectr
Note: This is only for ubuntu - https://docs.vectr.io/Installation—Ubuntu/
- Install pre-requisites if not already.
curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo apt-key add -
sudo add-apt-repository \
"deb [arch=amd64] https://download.docker.com/linux/ubuntu \
$(lsb_release -cs) \
stable"
sudo apt update
sudo apt-get install docker-ce docker-ce-cli containerd.io docker-compose unzip
sudo apt upgrade
sudo systemctl enable docker
- Download latest release zip from Vectr Git.
- Create a folder for Vectr,
eg: /opt/vectr - Unzip the downloaded zip to the target directory.
- Edit the
.envfile and change default passwords,COMPOSE_PROJECT_NAMEif desired.
# .env file
APP_NAME=VECTR
VECTR_HOSTNAME=sravectr.internal
VECTR_PORT=8081
# defaults to warn, debug useful for development
VECTR_CONTAINER_LOG_LEVEL=WARN
# If you supply a username:password in the URL, it will get overridden by MONGO_INITDB_ROOT_USERNAME and MONGO_INITDB_ROOT_PASSWORD
MONGO_URL=mongodb://vectr-mongo:27017/?authSource=admin
# MongoDB authentication username
MONGO_INITDB_ROOT_USERNAME=admin
# Change and store in a safe place
MONGO_INITDB_ROOT_PASSWORD= CHANGETHIS
# PLEASE change this and store it in a safe place. Encrypted data like passwords
# to integrate with external systems (like TAXII) use this key
VECTR_DATA_KEY=CHANGEMENOW
# JWT signing (JWS) and encryption (JWE) keys
# Do not use the same value for both signing and encryption!
# It is recommended to use at least 16 characters. You may use any printable unicode character
# PLEASE change these example values!
JWS_KEY=CHANGETHIS
JWE_KEY= CHANGETHISTOO
# This sets the name of your project. Will show up in the name of your containers.
COMPOSE_PROJECT_NAME=sandbox1
# This is where the mongodb mounts.
VECTR_DATA_DIR=/var/data/
- Run a docker-compose command to bring up the containers :
sudo docker-compose up -d. This will pull all required containers and spin up the containers.
If below error comes up, edit the docker-compose.yml file and change the ip in network config to some other ip not used by anything on your network.
ERROR: Pool overlaps with other one on this address space
networks:
vectr_bridge:
ipam:
driver: default
config:
- subnet: "${VECTR_NETWORK_SUBNET:-172.16.99.0/24}"
- Once containers are up, the SRA Vectr can be accessed at
https://<VECTR_HOSTNAME>:8081/whereVECTR_HOSTNAMEthe one mentioned in.envfile. In this casesravectr.internal.
- Use below credentials to login:
User: admin
Password: 11_ThisIsTheFirstPassword_11
- To stop containers.
sudo docker-compose stop
[vectr] sudo docker-compose stop
Stopping sandbox1_vectr-rta-builder_1 ... done
Stopping sandbox1_vectr-rta-webserver_1 ... done
Stopping sandbox1_vectr-tomcat_1 ... done
Stopping sandbox1_vectr-rta-redis_1 ... done
Stopping sandbox1_vectr-mongo_1 ... done
Importing Mitre CTI (STIX 2.0) to Vectr
To import TTP’s of specific APT group, we can use the import feature in Vectr.
- Goto MITRE CTI
- Download https://github.com/mitre/cti/blob/master/enterprise-attack/enterprise-attack.json
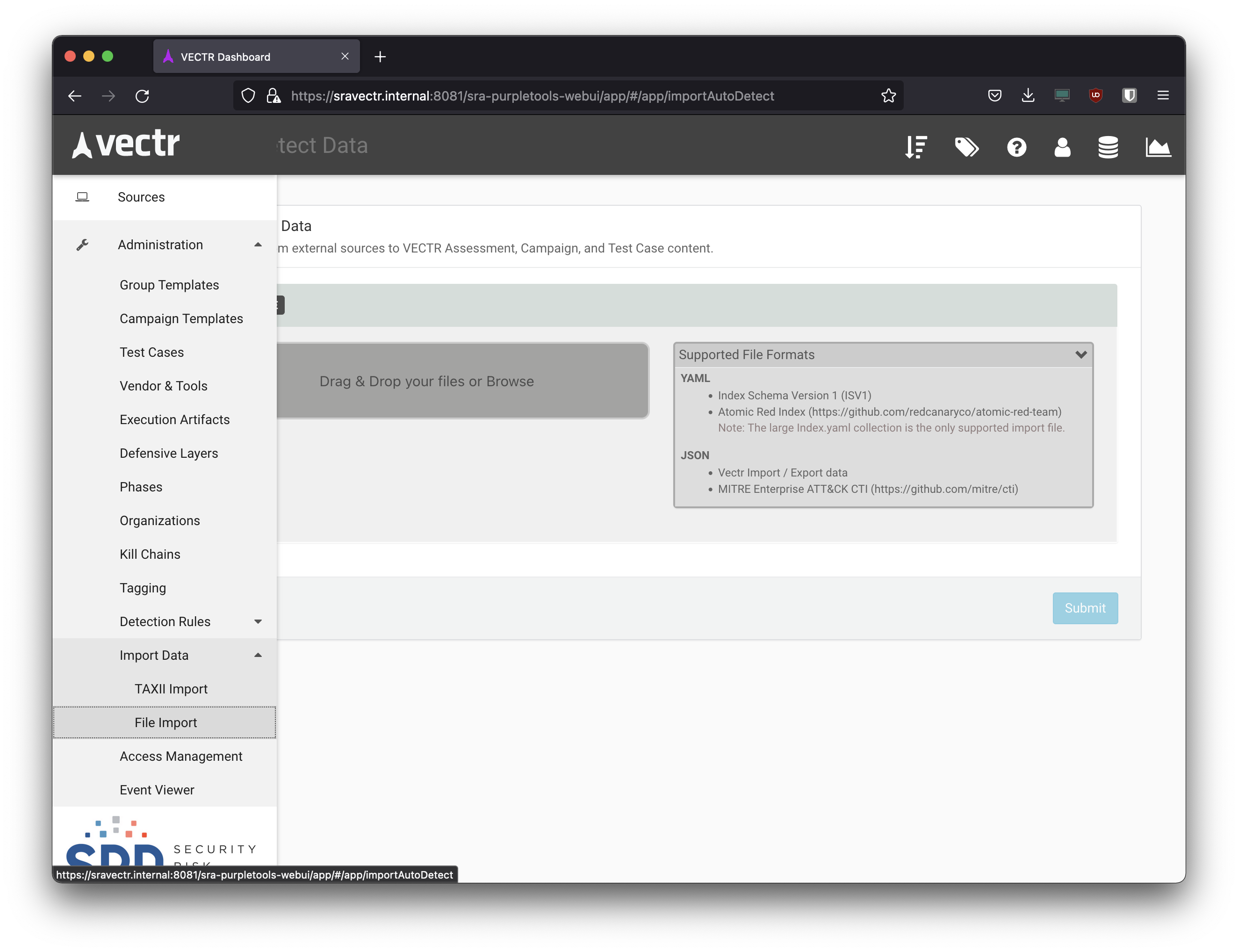
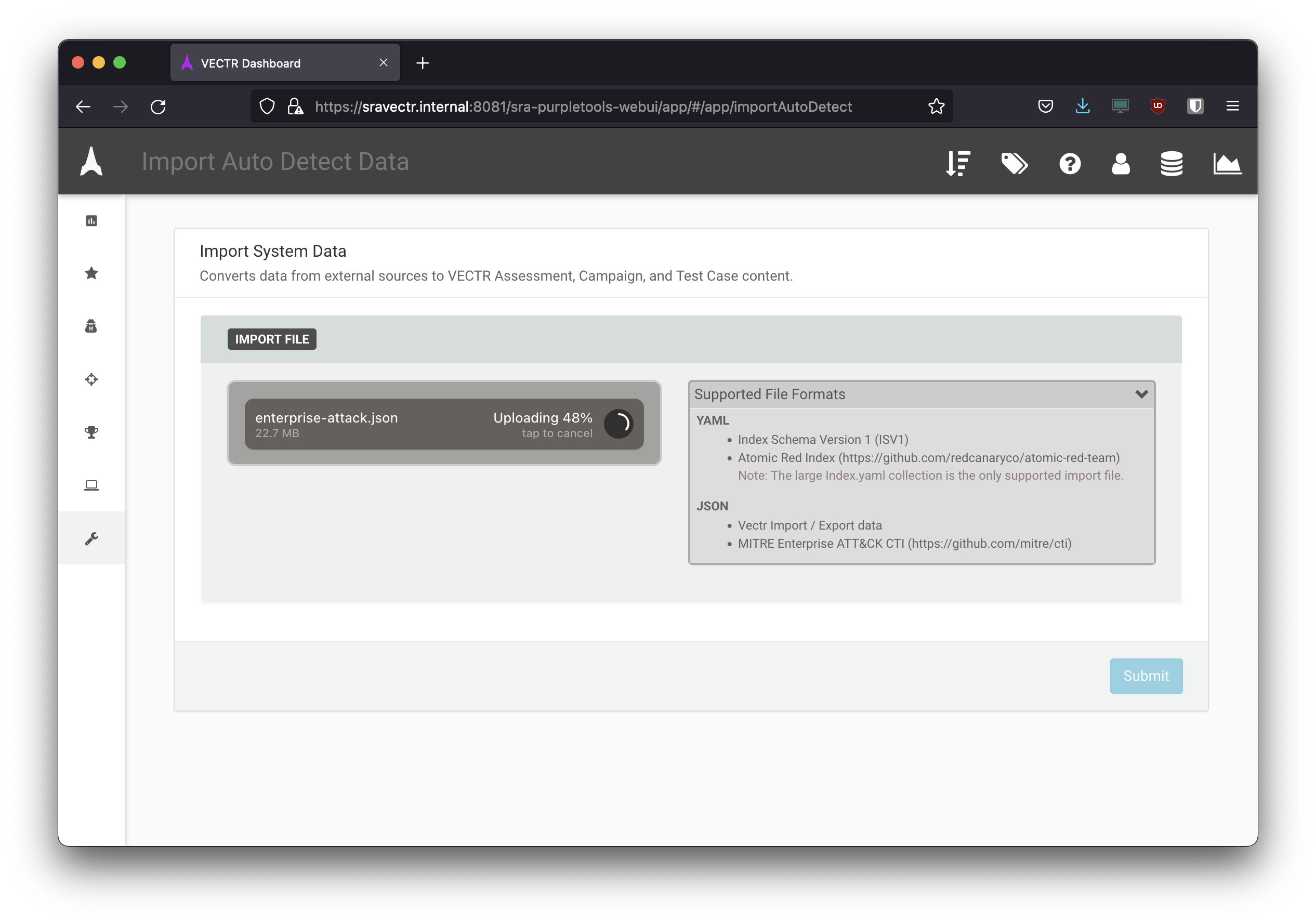
- In Vectr, navigate to
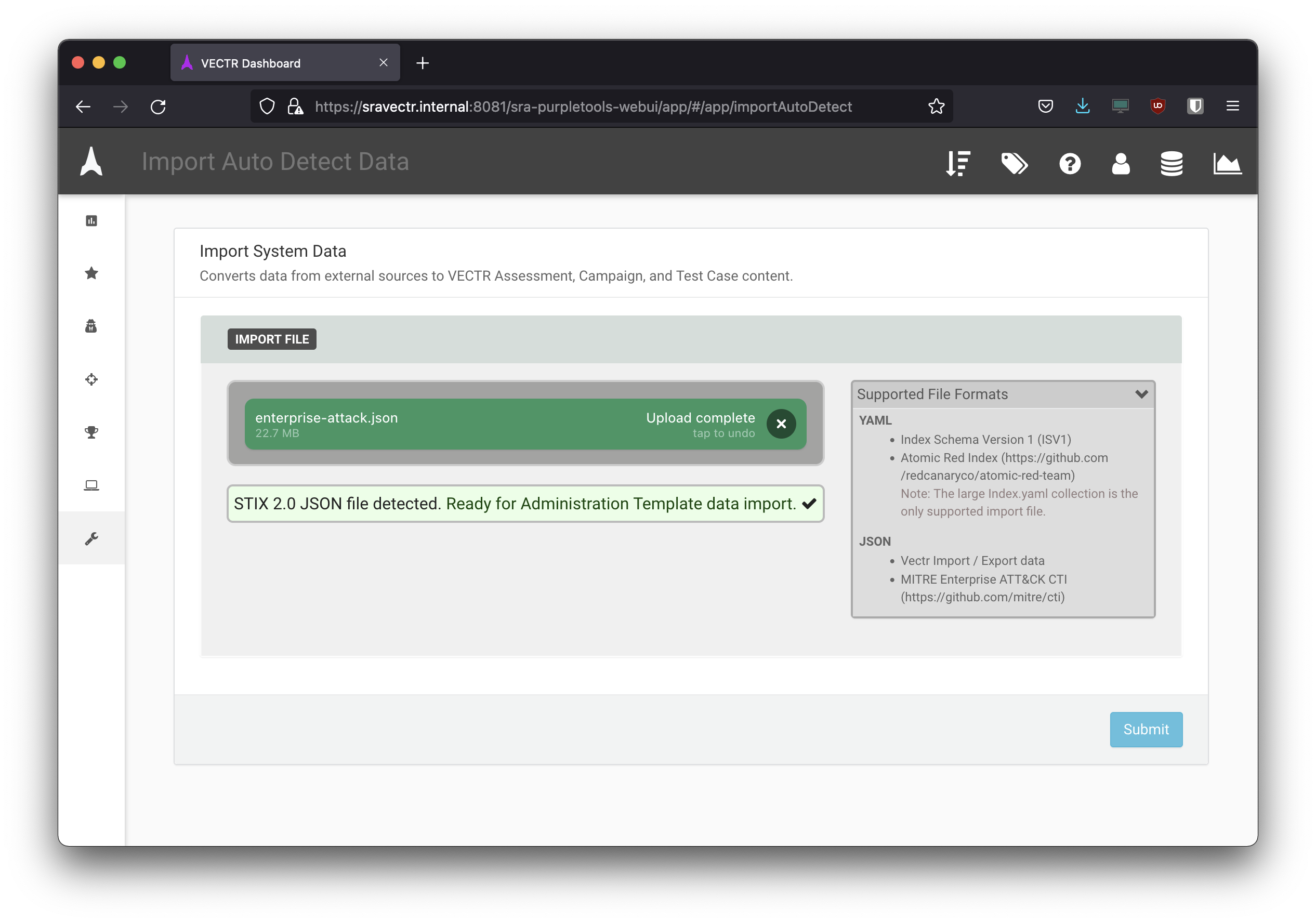
Administratration > Import Data > File Importand select the downloadedenterprise-attack.jsonfile. - Once uploading is complete, click submit so that Vectr will parse the file and list all APT groups and relevant TTP’s.
- Select the ones you want to import and submit.
- Once importing is finished, the TTP’s will be grouped under the APT groups name.
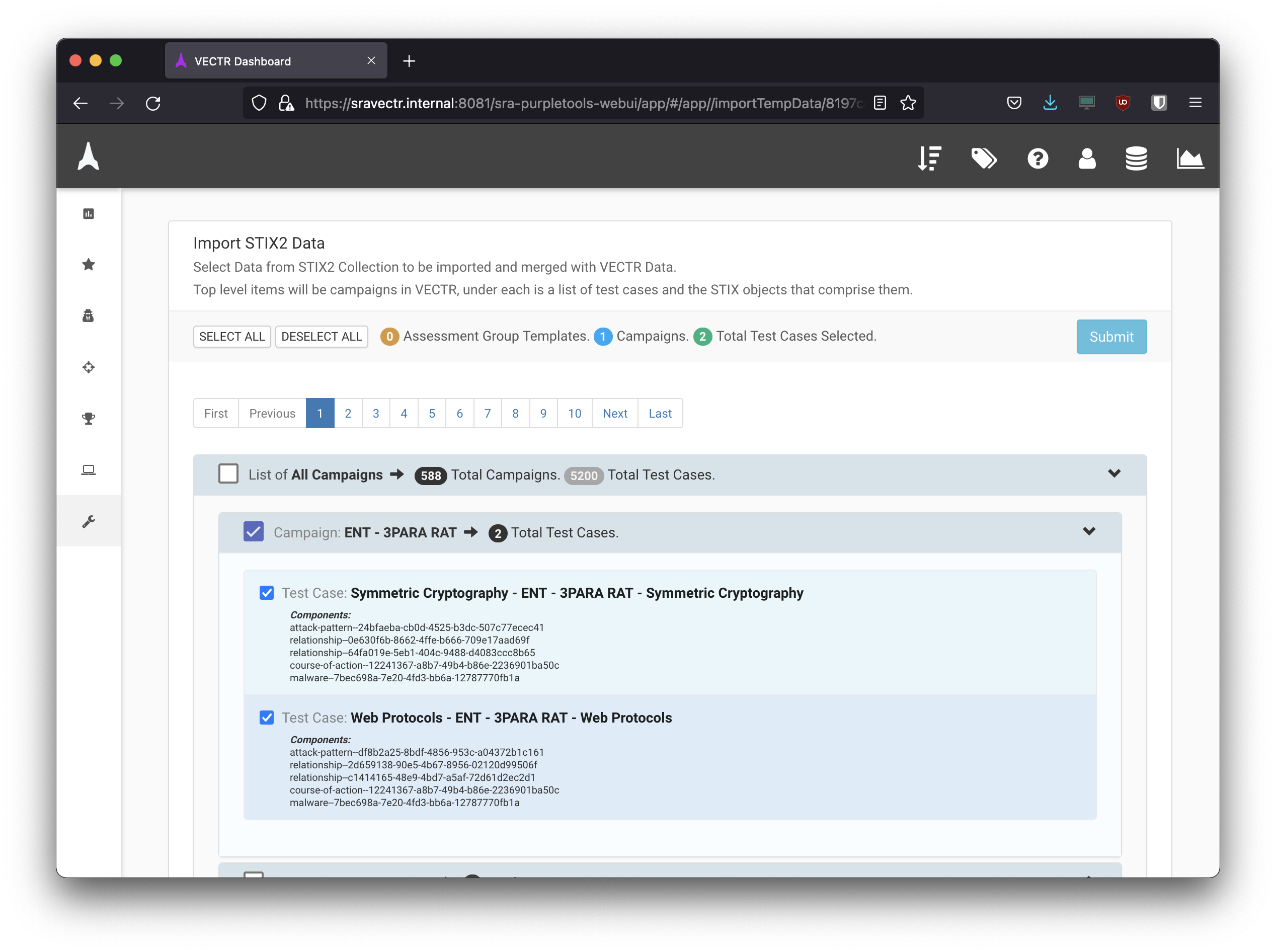
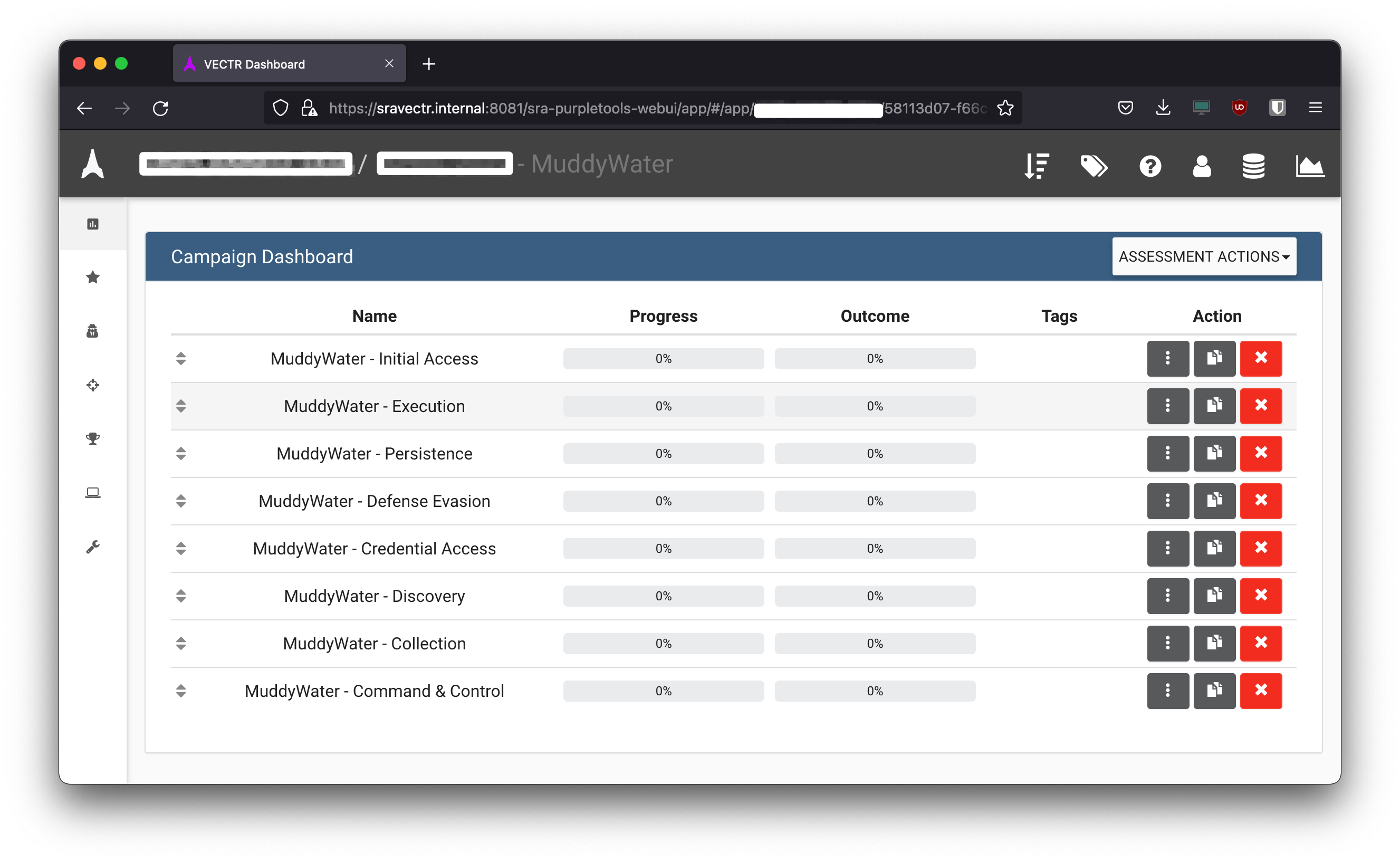
- When creating assessment, TTP’s can then be imported as a single campaign like below or each phase can be split.
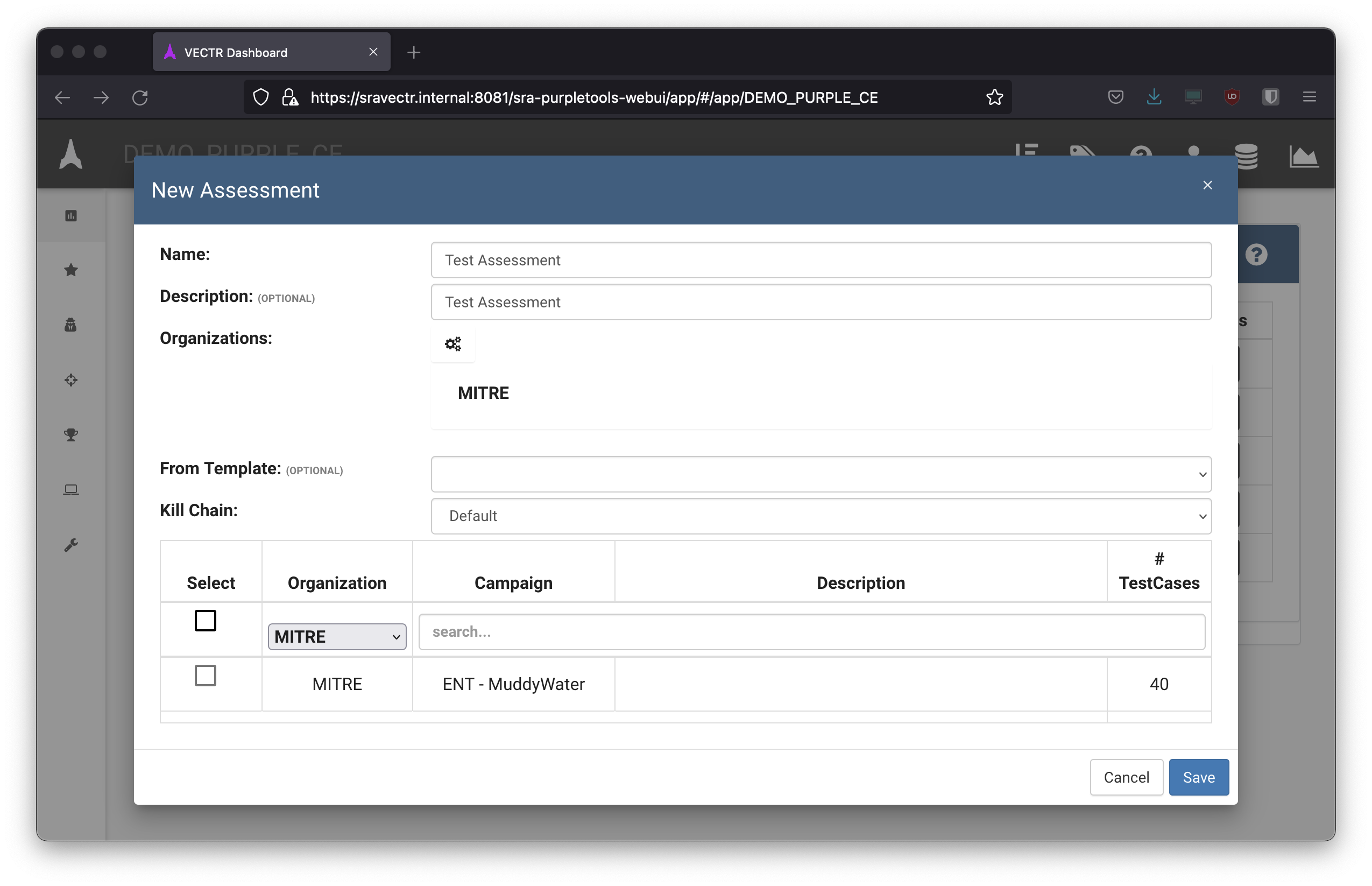
- Campaign split into different phases